The API ACL consist on a set of rules to allow API pass through.
This is the first layer of protection. A private ACL will require API Authentication and Permissions to act.
By default, all request will be allowed and new request will be added to this table for you to access. The control panel’s API ACLs will be automatically added when you build with the “with_api” parameter.
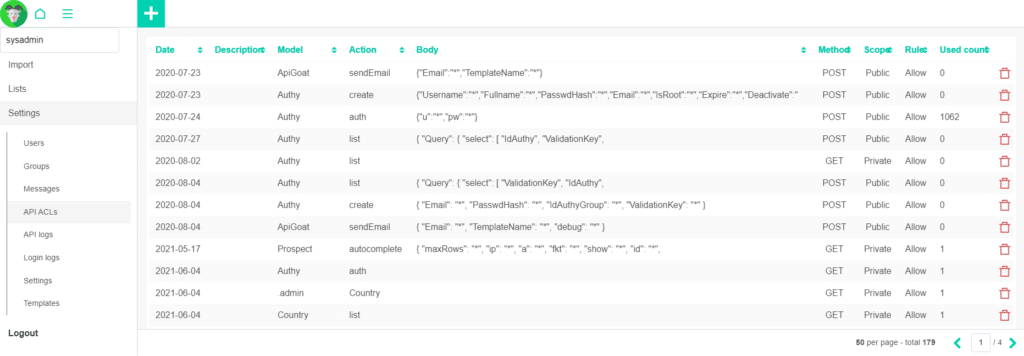
It is accessible via the Settings -> API ACL submenu.
In the Welcome page, the parameter “Current state of the App.” is used to switch from Development to Production. This will affect the RBAC from “allow all” to “deny all”.
Managing rules for better security
So the first time you use create a user via the API.
POST https://x.apigoat.com/api/v1/Authy HTTP/1.1
Content-type: application/json
Accept: application/json
{
"Username": "bob",
"Fullname": "",
"PasswdHash": "hash",
"Email": "example@domain.com",
"IsRoot": "No",
"Expire": null,
"Deactivate": "Yes"
}You possibly want this to be public, meaning that no login is required to create a new user following that some values are met, like that the created user is not root.
The first time your run the query, you will get
{
"status": "failure",
"error": "invalid-token",
"messages": "Token not found.",
"data": null
}The API expect you to authenticate first.
In the API ACL table, an entry will have been added with a Private scope, A Allow Rule for the Authy model and the create action.
Also the Rule body will look like this
{
"Username":"*",
"Fullname":"*",
"PasswdHash":"*",
"Email":"*",
"IsRoot":"*",
"Expire":"*",
"Deactivate":"*"
}
This rule denies this request public requests.
Permit some
To get this example to be public, meaning accessible without logging in first, you need too set the Scope to Public.
But this is dangerous, like that, a ill-intentioned third party could create an Active user with root privilege by sending
{
"Username": "bob",
"Fullname": "",
"PasswdHash": "hash",
"Email": "example@domain.com",
"IsRoot": "Yes",
"Expire": null,
"Deactivate": "No"
}To secure your API, you need to set restricted ACL. Some value must be fixed, specially for Public routes.
To do that, make sure the proper values are forced in the Body
{
"Username":"*",
"Fullname":"*",
"PasswdHash":"*",
"Email":"*",
"IsRoot":"No",
"Expire":"*",
"Deactivate":"Yes"
}This way, the only request to create a user with “IsRoot”:”No” and “Deactivate”:”Yes” will be accepted.

